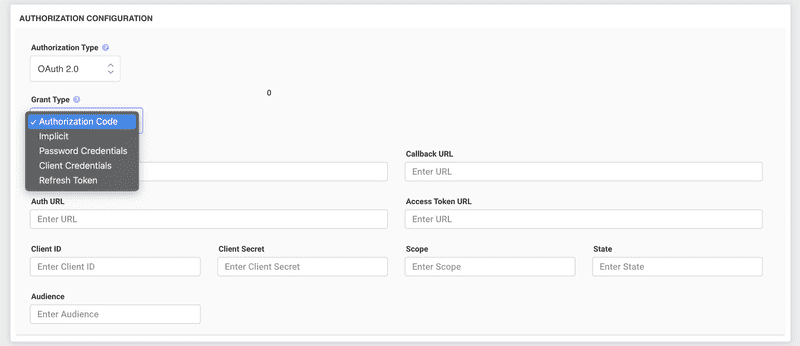
Authorization Code Grant Type in OAuth 2.0
The Authorization Code Grant Type is one of the most commonly used OAuth 2.0 grant types. It's specifically designed for applications that can confidentially maintain their client secret, making it ideal for server-side applications.
How Does Authorization Code Work?
- Redirection:
- The client application redirects the user to the OAuth 2.0 authorization server's authorization endpoint. This redirection typically includes query parameters such as the
client_id,response_type(set to "code"),redirect_uri(where the authorization server will send the user after granting/denying permission), andscope(which specifies the level of access the application is requesting).
- User Authentication:
- The user logs into the authorization server (if not already logged in) and reviews the access request by the client application.
- Authorization Code Issuance:
- If the user grants permission, they are redirected back to the client application via the
redirect_uriprovided earlier. The redirection also includes an authorization code in the URL.
- Token Exchange:
- The client application exchanges the authorization code for an access token by making a POST request to the authorization server's token endpoint. This request contains the authorization code,
client_id,client_secret,redirect_uri, andgrant_type(set to "authorization_code").
- Access Token Issuance:
- If the authorization server successfully verifies the provided code and client credentials, it returns an access token (and optionally, a refresh token) to the client application.
- Access Protected Resource:
- The client application uses the obtained access token to make requests to the resource server (API) on behalf of the user.
How to Configure Authorization Code?
- Register Your Application:
- Before starting the OAuth flow, register your application with the OAuth 2.0 provider. Upon successful registration, you'll receive a
client_idandclient_secret.
- Redirect URI Setup:
- When registering your application, you'll often be asked to provide a
redirect_uri. This URI is where the authorization server will send users after they grant/deny access. Ensure this URI is accurate and secure (typically using HTTPS).
- Implement the OAuth Flow:
- Use a library or SDK compatible with your application's language and framework to simplify this process.
- Begin the flow by redirecting users to the authorization server's authorization endpoint with the necessary query parameters.
- Implement an endpoint on your server that matches the
redirect_uriyou registered. This endpoint will handle the incoming authorization code. - Exchange the authorization code for an access token by making a POST request to the token endpoint.
- Secure the Client Secret:
- Never expose your
client_secretin client-side code. Only use it server-side when exchanging the authorization code for an access token.
- Token Storage:
- Once you have an access token, store it securely. Depending on your application's needs, this could be in server memory, a database, or a secure cookie. Always use HTTPS to ensure encrypted communication.
- Handle Token Expiry:
- Access tokens are often short-lived. If you have a refresh token, use it to get a new access token without needing the user to re-authenticate.
Final Thoughts on Authorization Code
The Authorization Code Grant Type is a robust and secure method for obtaining user authorization, especially for server-side applications. The additional step of exchanging an authorization code for an access token ensures that direct access to user credentials is avoided. When implementing, always prioritize security, using HTTPS and securely managing client secrets and tokens.